开始网鼎杯的jocker学习
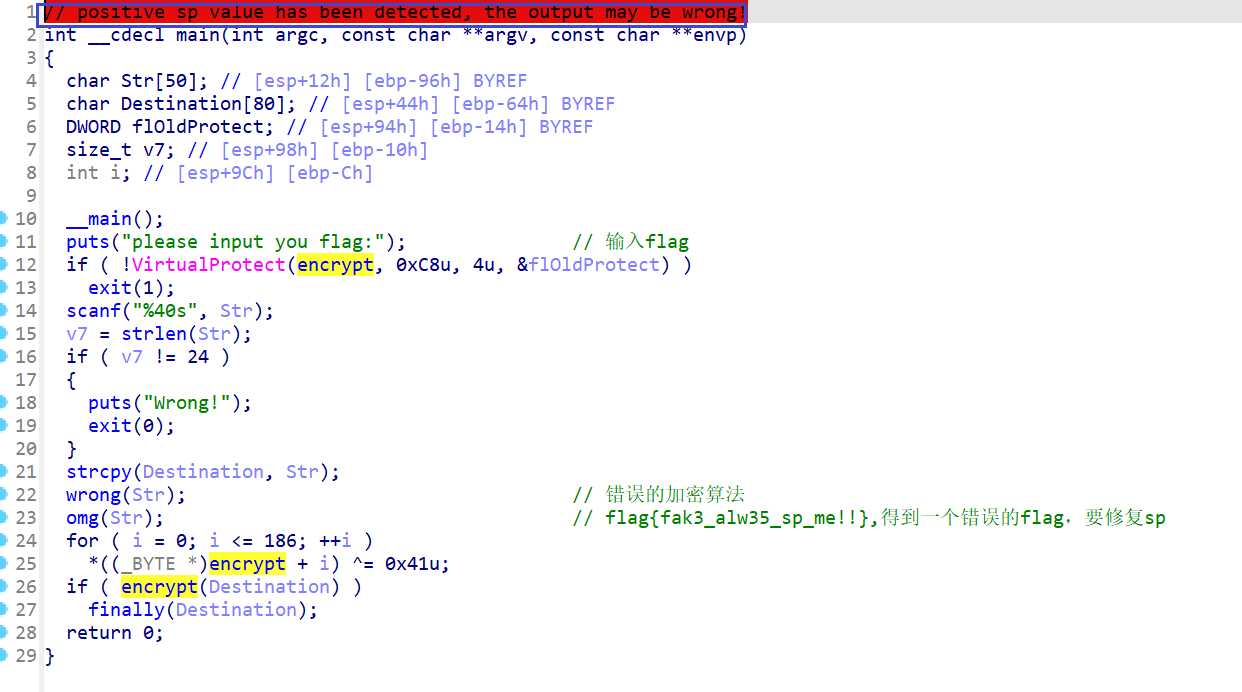
修复sp
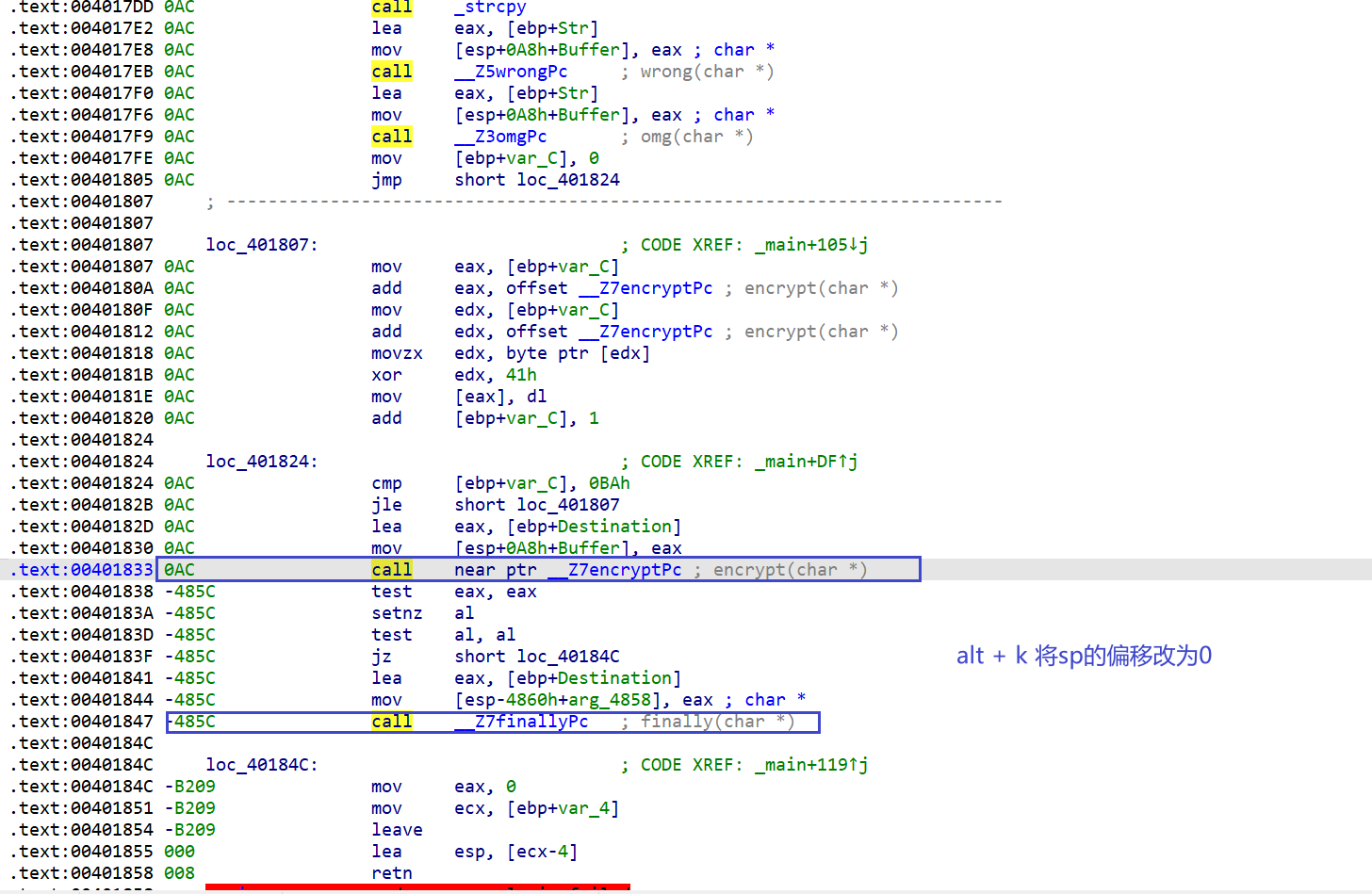
可是encrypt函数还是进不去
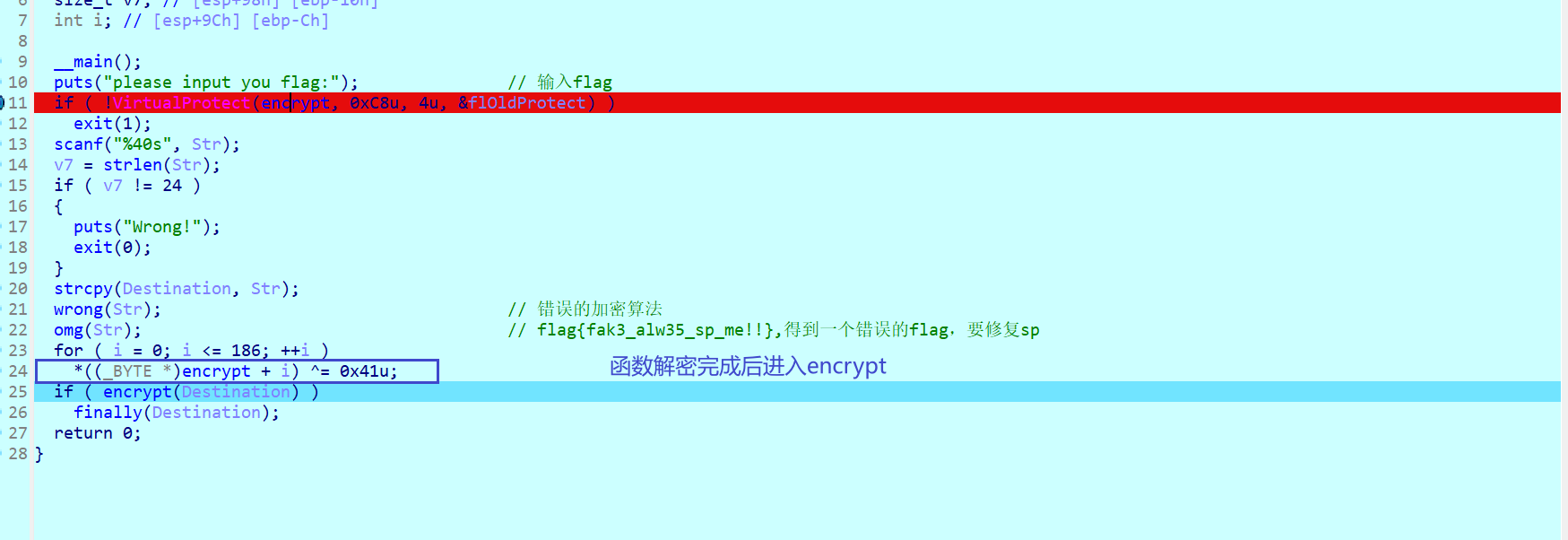
这是个smc动调解密函数,进入函数后从text:00401500的定义头道endp进行u(undefine)再在定义头p重定义函数。
1 | void __cdecl __noreturn encrypt(char *a1) |
得到加密函数
1 | # 预定义的 unk_403040 数组 |
得到了一半flag,我们刚刚分析的时候有个finally的函数进去看看
1 | int __cdecl finally(char *a1) |
根据最后一个字符 ‘}’ 猜测
1 | encrypted = "%tp&:" |
1 | flag{d07abccf8a410cb37a} |
